How to Learn Cyber Security Step-by-Step: A Complete Beginner’s Guide
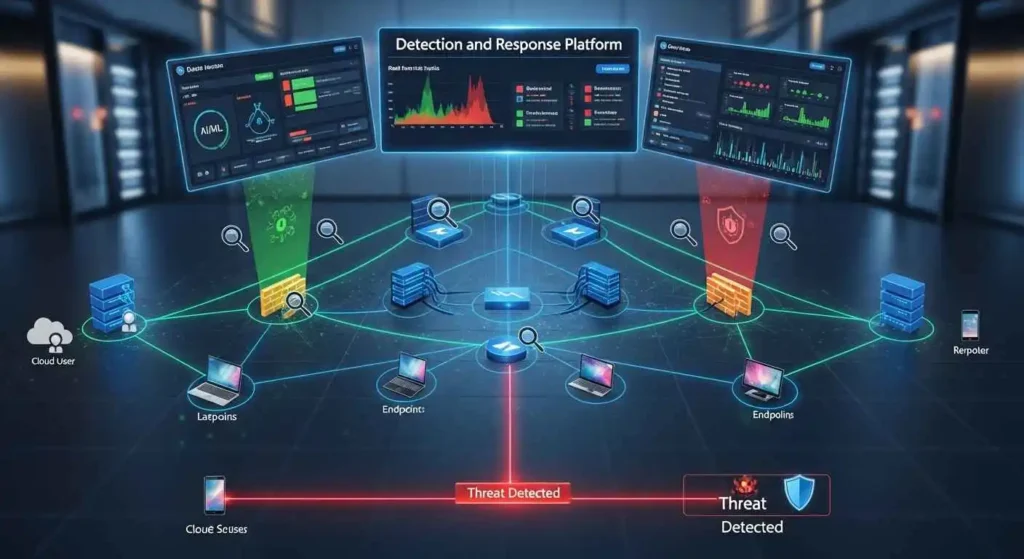
How to Learn Cyber Security Step-by-Step: A Complete Beginner’s Guide In the digital age of today, cybersecurity has become a necessity for survival. Millions of people are exposed to threats such as phishing and malware. They also face identity theft, ransomware, and other types of cybercrime. The good news is? It’s not necessary to be a tech genius to start […]
How to Learn Cyber Security Step-by-Step: A Complete Beginner’s Guide Read More »